Thanks in part to the U.S. government's meaningful use initiative, U.S. hospitals have increased security to protect their electronic records, according to the fifth annual security survey from the Healthcare Information and Management Systems Society (HIMSS). Physician practices, however, have not been as progressive.
The results of the 2012 HIMSS Security Survey, supported by the Medical Group Management Association (MGMA) and underwritten by Experian Data Breach Resolution, were published on December 12. They present a mixed message on the preparedness of U.S. healthcare providers to adequately secure healthcare data in an increasingly electronic environment.
More healthcare organizations, particularly hospitals, are conducting an annual security risk analysis, a requirement of the electronic health record incentive program from the U.S. Centers for Medicare and Medicaid Services (CMS).
But is what's being done enough? The report doesn't specifically say, instead offering a comparison of results reported in the first survey conducted in 2008. Many findings, five years later, are remarkably similar.
Who participated
The survey was completed by 303 individuals, all of whom had jobs directly involved with security and/or IT activities. Fifty-five percent reported that they worked at an ambulatory care physician practice, 24% worked at a specific hospital, and 18% worked at a multifacility enterprise or healthcare facilities corporation. Two-thirds of respondents reported that they were responsible for ensuring the safety of their organization's data on a day-to-day basis. Approximately half were either chief information officer or vice president of IT at their organization.
Geographic representation was uneven. Only 5% of respondents were from states in New England. By comparison, there was about a 20% response rate from individuals in the East North Central region and the South Atlantic region as defined by the U.S. Census Bureau. Other regions averaged about 10%.
Security budgets
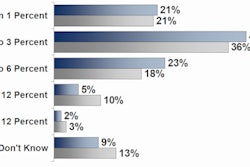
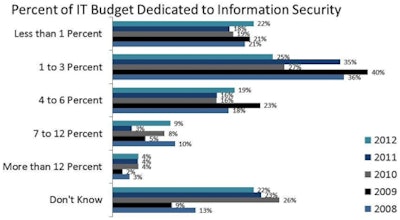
The overall percent of IT budgets spent on information security has remained relatively unchanged over the past five years. In 2008, 57% of respondents reported that they spent 3% or less of their IT budget on information security, and in 2012 only 47% did. This year, 22% again reported that their budget was less than 1%.
Physician practices spent more of their IT budgets on security than hospitals. As an example, 6% of ambulatory facilities spent more than 12% of their budget, compared with less than 1% of hospitals.
 |
| Image courtesy of 2012 HIMSS Security Survey. |
However, except for 4% of respondents who said no one in their organization was responsible for security, staff resources have increased over the years. Nearly two-thirds of respondents said they had a full-time resource, about one-third had part-time resources, and less than 1% outsourced security management.
Risk analyses and audit logs
More than 90% of hospital respondents and 65% of physician practice respondents conducted a risk analysis, with two-thirds of the total reporting that they conducted this annually. Only 7% conducted a risk assessment semiannually; 25% did so biannually.
In situations where a risk analysis identified a deficiency, about half corrected the situation within six months and 38% did so within a year. This represents a higher level of responsiveness than was reported in 2011.
Fewer than half tested their data breach plan on an annual (19%) or semiannual (19%) basis. Response was higher in terms of auditing an organization's IT security plan. Three-fourths of hospital-based and about half of physician-practice-based respondents said that they did this, with the majority conducting tests on an annual basis.
Conducting audit logs and analyzing this information was the predominant means of monitoring security at hospitals. Surprisingly, the survey of physician practices did not ask this question. Clinicians' access to data was heavily monitored, as were logs of firewall and server-related activities. About half (56%) analyzed data from intrusion detection systems, and only 10% monitored activity of storage devices. Seventy percent reported that they analyzed audit logs of security-critical events and nonclinician access to data.
Data breaches occurred in 31% of hospitals and in 15% of physician practices, with most breaches caused by equipment theft. Three-fourths of the hospitals and half of the physician practices had established policies to deal with a security breach.
Only one-fourth of all respondents said they encrypt information on mobile medical devices. Two-thirds, however, encrypt information on laptop computers and about half encrypt on servers.
Data sharing
In an era of greater access to data, healthcare organizations are continuing to deploy increasingly sophisticated software tools to control access. But there is room for improvement. Only a single method of controlling employee access (predominantly password-based) was reported by more than half of respondents. Thirteen percent of hospital-based and 5% of physician-practice-based respondents used a combination of four or five methods.
Yet 73% provided access to electronic patient information to patients and other healthcare providers. Nearly 40% offer Web portal access to their patients, with all but 3% of these respondents controlling access via a unique ID or patient-selected password. Approximately 18% track patient access to their medical records.
What does HIMSS and its 44,000 individual members think about the 2012 survey findings? Lisa Gallagher, senior director of privacy and security at HIMSS, made this comment: "More hospitals and physician practices have increased their emphasis on security of patient health data, but have more to accomplish when it comes to ongoing data security."
Whether the healthcare industry has progressed or stagnated regarding its level of security is still up for debate, along with the question of whether healthcare data are as secure as other personal data managed by other industries.
Click here to access the 2012 HIMSS Security Survey report.