NEW ORLEANS - When Hurricane Katrina ravaged this city in 2005, security immediately became a top concern for law enforcement and residents. Security is as subtle and powerful as the steadily rising floodwaters that destroyed entire neighborhoods here. Without it there is chaos. With it there can be calm before and after the storm.
Issues surrounding data security are finally becoming more prevalent in healthcare, as was evidenced at this year's Healthcare Information and Management Systems Society (HIMSS) conference. Although multiple sessions touted various concepts, a common theme was educating the industry on how to better plan for security.
What is security? A common misconception is that it is just who has access to what, when, and with what privilege. A broader scope of security encompasses the full "CIA" triad: confidentiality, integrity, and availability.
Confidentiality refers to who has access to what data, when, and with what privilege. The "I" component addresses the integrity of the data while at rest or in transmission. As institutions become more dependent on digital data for patient care, the ability to access that data, when and where it is needed, becomes critical. It is this availability component that completes the CIA triad.
A security plan addresses the vulnerabilities, threats, and risks that potentially could impact the CIA of an institution's data.
In a preconference tutorial on information security, Overland Park, KS-based healthcare IT consultant Tom Walsh discussed the challenges of positioning the costs of implementing a security program with institutional management. He used the concept of return on investment (ROI) versus cost avoidance to illustrate how management would perceive these costs in the implementation of a security program.
Although ROI is the profit or growth on an investment, cost avoidance is the mitigation of a negative financial impact. With security, there is no tangible ROI; therefore, a security program's benefits are derived from the potential cost avoidance.
Walsh stressed that enterprise compliance is not a point-in-time event, but rather an ongoing process. Components of this process include:
- Business impact analysis
- Risk analysis
- Risk management
- Developing a plan
- Education, training, and awareness
"Understanding (the) business is more important to the success of a security program" than the technology, Walsh stated.
He emphasized education, training, and awareness as key components of any successful security program. The user community must be educated about the importance of security but they must also be trained on how to implement and execute the requirements of a security program. Walsh used the example of sex education compared with sex training -- most parents are not opposed to sex education in schools yet cringe at the thought of sex training.
Knowledge, in theory, enables an institution to plan for all contingencies. The reality, though, is that we don't have knowledge of all the possible things that can happen. For any risk analysis, an institution must determine the risks, prioritize the likelihood of occurrence, and address those issues that pose the greatest risk.
Walsh pointed out that a few of the top five threats are from internal sources -- employee errors, malicious and nonmalicious access to records, and disgruntled employees committing intentional acts. The underlying message from Walsh is that facilities must strive to address the security issues before they become a "60 Minutes" moment.
In addition to Walsh's in-depth tutorial, other sessions dealt with more granular aspects and results of security programs. An education session titled "Disaster Recovery -- Averting the Perfect Storm" presented a case study of how Illinois- and Indiana-based healthcare network Provena Health addressed disaster recovery planning. Other education sessions at the conference delved into the technical issues involved with implementing security at various levels throughout a healthcare enterprise.
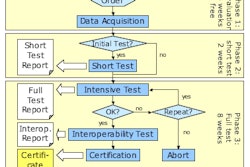
The Integrating the Healthcare Enterprise (IHE) initiative is also addressing the issues of enterprise- and regional health information organization (RHIO)-level security through its privacy exhibit at the interoperability showcase. The demonstration followed the path of a patient from an ambulatory care system into an acute care environment, allowing the records to follow the patient through the process using newly accepted standards, while maintaining a high level of security and privacy.
The IHE is attempting to leverage the prevailing security standards to improve the way security is applied across the healthcare enterprise. This effort is complicated by the fact that healthcare institutions have a wide spectrum of security programs -- from comprehensive to minimal -- and at the vendor level there is a wide array of tool sets, some robust and some marginal.
Regardless of the technology deployed for security, it is people who make the difference. Applying the most advanced technology to a problem won't matter if users are untrained, or lack adequate understanding of security program's values. Without a successfully implemented security program, the institution risks becoming a headline.
By John S. Koller
AuntMinnie.com contributing writer
March 2, 2007
Koller is president of healthcare information technology consulting firm KAI Consulting of Larkspur, CO. He can be contacted at 303-681-2854 or via the company's Web site.
Related Reading
Regulatory carve-outs hope to spur HIT growth in U.S., February 28, 2007
EHR deployment presents familiar obstacles, February 27, 2007
U.S. takes steps to ramp up HIT efforts, February 23, 2007
Security considerations in transmitting medical information, January 19, 2007
HIPAA security still problematic, November 7, 2006
Copyright © 2007 AuntMinnie.com