A new hacker group called Orangeworm has developed a computer virus that specifically targets the healthcare sector. The virus has already been detected on devices such as x-ray and MRI machines, according to a warning issued on April 23 by antivirus firm Symantec.
Orangeworm has developed a Trojan horse virus called Kwampirs that tries to work its way into targeted computer networks through back doors, or secret portals that enable access to a computer network without detection. Some 39% of sites affected by Orangeworm activity are within the healthcare sector, according to Symantec.
The company said Orangeworm has installed Trojan.Kwampirs "within large international corporations that operate within the healthcare sector in the United States, Europe, and Asia." Targets include healthcare providers, pharmaceutical firms, and IT software developers for healthcare OEMs. The most likely goal of the attacks is "corporate espionage," the bulletin noted.
"We believe that these industries have ... been targeted as part of a larger supply-chain attack in order for Orangeworm to get access to their intended victims related to healthcare," Symantec said.
What's more, Orangeworm appears to be selecting its targets "carefully and deliberately," according to the company. The group does not appear to be connected to any organized state or entity and its motives are unclear.
In addition to the Kwampirs virus being found on software used to control imaging scanners, Orangeworm appears to be interested in computers used to help patients fill out consent forms for medical procedures.
When Orangeworm gains access to a target site's computer network, it deploys Trojan.Kwampirs, which gives the group remote access to the infected computer. Kwampirs then decrypts and extracts a copy of its main dynamic link library (DLL) payload, according to Symantec. The virus also takes other steps to avoid detection, and it executes a series of commands to gain information about the infected network.
Kwampirs tries to replicate by copying itself over network shares. While "this method is considered somewhat old," it could work for computer networks that still have older operating systems like Windows XP. "This method has likely proved effective in the healthcare industry," Symantec said.
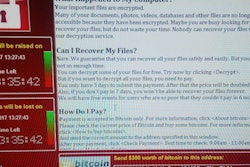
Indeed, the WannaCry ransomware attack that shut down imaging facilities in the U.K. and Scotland last year is believed to have entered hospital computer networks through vulnerabilities in devices such as contrast injectors that hadn't received updates and were running Windows XP.
The Symantec bulletin offers several steps that companies can take to protect their computer networks, and the firm has developed specific tools for detecting Trojan.Kwampirs.